Hello everyone,
In this article, I would like to share my experience of the webinar that I have attended on March 8 on the Topic Industry Usecase of Kubernetes
Got to know so many new things and I have learned a lot from the webinar.
Topics that were discussed in the webinar were:
- Modernization
- System Design Banking
- Security Use Case for OKD/Open Shift
Moderization
Migrating the code from Centralized Version System to Distributed Version System is called Modernization.
GIT is preferred over CSV ( Centralized Version System )
Git is preferred over CVS because git reduces the workaround time, it provides an agile sprint way of working, and Jenkins integration can be done with git.
- Distributed Works better if there is a big team
- Easy to create branches in Git
- Git UI gives the more clear picture of the repos
- Rest API implementation in Git
- Git is easy to reconcile
- Code merges between the branches.
- CVS works on a file level, Git works on a repo/ module level
System Design Banking
- Kubernetes Architecture
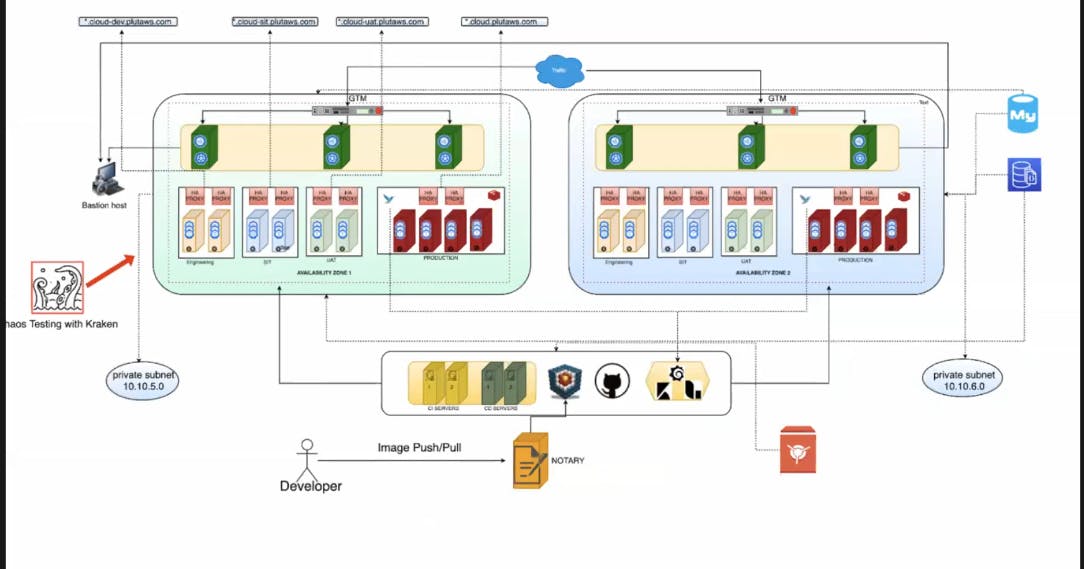
GTM is a Global Traffic Manager, GTM is designed so that Internet users can more reliably get to the websites or any other application.
We need different environments in Production so that different people can work on the project and can release multiple versions at the same time.
Chaos testing is used to test service in the worst-case scenario like in worst-case scenario how will service work.
- CPU request: It is the minimum CPU allocated to the microservices
- Cpu limit: It is the maximum CPU allocated to the microservice
- CPU Leak: means when the program required more CPU but the CPU doesn’t release the resources & it continuously goes on allocating more CPU than the limit
Security Use Case for OKD/Open Shift
If the customer wants to deploy the application to the production environment, with the following conditions:
- Run-on specific user ID
- Should not use any Linux privileges
- Have specific capabilities
- Not use PVCs
The solution to this problem is that we can create our own Customized Security Context Constraints (SCCs) and apply it to our application.
" Security context constraints (SCC) is use to control the actions that a pod can perform and what it has the ability to access."
What SCCs can control?
- Whether a pod can run privileged containers
- The capabilities that a container can request
- The use of host directory as volumes
- SELinux context of a container and many more
It was an amazing webinar got to learn directly from the experts, many doubts were clear and many new things came to know. Learn about how the IT industry really works and what technologies are required and how technologies are integrated.
And the best things was that experts were our seniors that gave us immense motivation to work hard and can become experts one day⭐
Thank you to the experts and LinuxWorld team for organizing the Webinar ✨
